Products
Surveillance systems

1
Facial Recognition Systems
A facial recognition system is a technology used to identify individuals by comparing their facial features with a pre-existing set of images or other biometric data. This system employs artificial intelligence and image analysis techniques to determine personal identity based on each individual’s unique facial characteristics. It is utilized in a wide range of applications such as security, attendance management, identity verification in electronic applications, and other fields.
Key Features and Applications:
- Security: Facial recognition systems are widely used for enhancing security in various environments such as airports, public spaces, and secure facilities by identifying unauthorized individuals and potential threats.
- Attendance Management: In workplaces and educational institutions, these systems help in automating attendance tracking, ensuring accurate and efficient record-keeping.
- Identity Verification: Used in electronic applications, such as banking and mobile devices, to verify the identity of users, adding an additional layer of security to protect against fraud and unauthorized access.
- Access Control: Facilitates secure access to restricted areas by allowing entry only to recognized individuals, enhancing the overall security of sensitive locations.
- Customer Experience: In retail and hospitality sectors, facial recognition can be used to personalize customer experiences, offering tailored services based on customer preferences and history.
The integration of facial recognition technology across these various applications enhances efficiency, security, and user convenience, making it a valuable tool in modern technological infrastructure.

2
Instant Alarm Systems
Instant alarm systems are systems designed to promptly and immediately trigger an alert in the event of an unwanted or emergency occurrence. These systems rely on a set of devices and equipment such as sensors, alarm devices, and communication devices. When an unusual or suspicious event is detected, whether it is a fire, gas leak, or building intrusion, the instant alarm system is activated, alerting relevant individuals to the danger through audible or visual alarms, or even through phone or electronic communications. These systems play an important role in enhancing the safety of individuals, properties, and various sites, contributing to reducing losses and facilitating evacuation and rescue operations in emergencies.

3
Guard Tour System
Guard Tour system is used to organize and manage security and surveillance operations at specific sites such as buildings, industrial facilities, residential complexes, government facilities, and more. The aim of this system is to ensure the safety and protection of properties and individuals at various locations.
The core operation of a patrol system involves establishing patrol routes for guards around the site, where guards move along these routes periodically and regularly. The schedule and routes are determined based on a risk analysis of the site and its specific security requirements.
Advanced technologies are usually employed to support the patrol process, such as GPS tracking systems and wireless radios for communication between guards and the control center, as well as data recording and reporting systems to document the safety of patrols and observations made by guards during their rounds.
The patrol system is a fundamental part of security and protection strategies to ensure the effectiveness of security measures and preventive actions at important sites.

4
Remote Surveillance Camera Solutions
Remote surveillance camera solutions refer to systems that allow users to monitor and record video footage from cameras placed in distant locations. These solutions use network connectivity, such as the internet or local area networks (LANs), to transmit live video streams in real-time or store recordings for later viewing.
Benefits of Remote Surveillance Camera Solutions:
- Remote Monitoring: Users can access live video footage and recordings from anywhere with internet access, using computers, smartphones, or tablets.
- Enhanced Security: By providing continuous monitoring, these solutions help deter intruders and unauthorized activities, thereby enhancing the security of homes, businesses, and public places.
- Flexible Deployment: Cameras can be installed in various indoor and outdoor locations, allowing flexible deployment based on specific surveillance needs.
- Scalability: Remote surveillance systems typically accommodate multiple cameras, making it easy to expand the system as surveillance requirements grow.
- Alerts and Notifications: Some systems offer motion detection and alert features, notifying users of any suspicious activities detected by the cameras.
- Evidence Collection: Recorded footage can serve as valuable evidence in investigations related to security incidents, thefts, or other illegal activities.
Overall, remote surveillance camera solutions provide users with peace of mind, convenience, and enhanced security by enabling remote monitoring and surveillance of their surroundings.
5
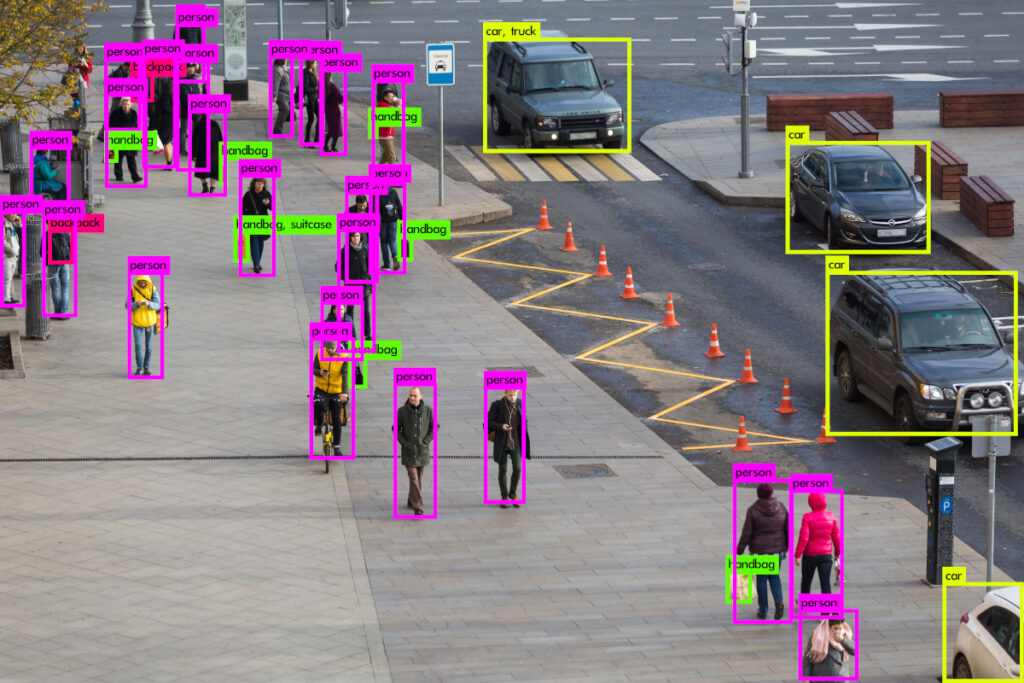
Analytics Cameras and Video Management Systems (VMS)
These are technologies and systems used to monitor, record, and manage video in various environments such as commercial buildings, factories, schools, parks, and more. Analytics cameras and VMS work together to provide effective visual monitoring and advanced video management.
- Analytics Cameras:
- These cameras have the capability to analyze visual data and apply artificial intelligence techniques to recognize objects such as faces, vehicles, movement, and more.
- They are used to detect unwanted events such as intrusions, large gatherings, and unusual movements.
- Video Management Systems (VMS):
- These are software solutions used to manage, store, review, and analyze video clips recorded from surveillance cameras.
- They provide a user-friendly interface for viewing live and recorded video, managing camera devices, and adjusting settings.
- They enable searching for video clips and generating detailed reports on recorded events and activities.
These technologies and systems work together to provide a comprehensive and effective visual monitoring system, allowing for intelligent analysis of visual data and prompt, effective action when necessary.

6
Thermal Cameras
Thermal cameras are a type of camera used to detect heat and capture images based on temperature differences rather than visible light. These cameras rely on thermal sensing technology to record the thermal radiation emitted by a target object and convert it into a thermal image that can be interpreted and analyzed.
Advantages of Using Thermal Cameras for Security:
- Ability to See in Harsh Environmental Conditions: Thermal cameras can detect objects even in complete darkness and perform excellently in adverse weather conditions such as fog and dust.
- Identifying People and Objects Based on Temperature: These cameras are used to detect individuals or objects emitting unusual heat, aiding in the detection of fires, unauthorized activities, or intrusions.
- Data Analysis and Integration with Security Systems: Thermal camera data can be analyzed and integrated with other security systems such as alarm systems and video management systems to achieve a comprehensive and effective security solution.
Applications:
Thermal security cameras are widely used in various security applications, including:
- Protecting critical facilities
- Border surveillance
- Industrial monitoring
- Fire incident management
- Search and rescue operations
- Intrusion detection
By utilizing thermal cameras, security operations can be significantly enhanced, ensuring robust protection and efficient monitoring in diverse environments.

7
Drones
Drones, also known as unmanned aerial vehicles (UAVs) or unmanned aircraft systems (UAS), are aircraft operated without a human pilot onboard, controlled either autonomously or via remote control. These drones are used in a wide variety of military and civilian applications, depending on their design and capabilities.
Uses of Drones:
- Reconnaissance and Surveillance: Drones are used to obtain precise aerial images and intelligence information from uninhabited or dangerous areas without risking the lives of crew members.
- Military Intelligence: They can be employed in military missions for reconnaissance and surveillance, flying over suspicious military zones.
- Aerial Photography and Videography: Drones offer high-quality aerial photography and videography for promotional purposes or general recordings.
- Environmental and Agricultural Monitoring: Drones are utilized to monitor environmental phenomena such as climate changes and pollution, and to aid in the management of natural and agricultural resources.
- Search and Rescue: They can be deployed in search and rescue operations to locate victims in natural disasters or accidents.
Advantages:
Drones are notable for their ability to fly for extended periods without needing to refuel and can be remotely controlled from a ground control station. This makes them a valuable tool for a wide range of applications.

8
Electronic Article Surveillance (EAS) Systems
Electronic Article Surveillance (EAS) systems are security systems used to prevent theft in stores and other commercial outlets. These systems rely on various electronic technologies to detect items that may be stolen or unpaid for when attempting to pass beyond the appropriate payment area.
Components of EAS Systems:
- EAS Tags: These consist of devices attached to merchandise, either as labels, security tags, or removable magnetic devices. These tags are deactivated at the point of sale when items are properly paid for.
- EAS Sensors: These sensors are usually installed at the store’s entrances or exits. They receive signals from the EAS tags when they are improperly deactivated, alerting staff to the presence of unpaid items.
- Alarm System: This system is triggered when an improperly deactivated EAS tag is detected, resulting in an audible or visual alarm to alert staff of a potential theft attempt.
Benefits and Applications:
EAS systems work to reduce theft incidents and enhance security in commercial environments by alerting staff and customers to theft attempts. They are commonly used in retail stores, department stores, and large shopping centers to protect merchandise and increase security.
9
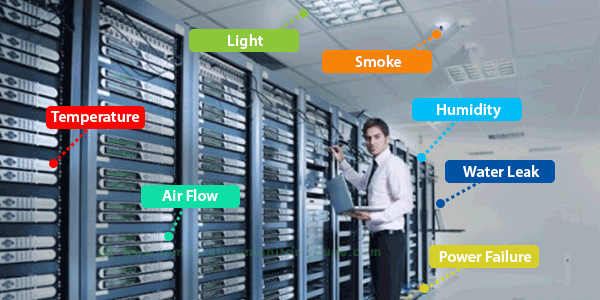
Temperature and Humidity Monitoring System
A temperature and humidity monitoring system is used to measure and monitor the temperature and humidity levels in a specific environment, whether indoors or outdoors. The aim of this system is to provide a comfortable and safe environment for work or living, and to ensure the quality of air and suitable conditions for various activities.
Components of Temperature and Humidity Monitoring Systems:
- Temperature Measuring Devices: These are used to measure the temperature in the environment being monitored, including digital thermometers or environmental thermometers.
- Humidity Measuring Devices: These are used to measure the humidity level in the environment, including relative humidity meters and hygrometers.
- Monitoring and Control Devices: These allow users to monitor readings and data related to temperature and humidity, and provide the capability to adjust and control the surrounding conditions.
- Alarm Systems: These provide immediate alerts when certain temperature or humidity levels are exceeded, allowing for timely corrective actions.
Applications:
This system is used in a variety of applications, including the food and pharmaceutical industries, hospitals, scientific laboratories, offices, homes, and commercial buildings. Temperature and humidity monitoring systems play a crucial role in ensuring the safety of materials and equipment and the comfort of people in different environments.

10
Fire Alarm System
A fire alarm system is an integrated system used to detect and alert people in the event of a fire or smoke detection in a specific location, helping to take necessary precautions to prevent fire and save lives and property.
Components of a Fire Alarm System typically include:
- Fire Detection Devices: These include smoke and heat detectors that monitor the environment surrounding the location. Upon detecting smoke or a rise in temperature, they send out an alarm signal.
- Alarm Devices: These receive signals from the fire detection devices and emit a loud and appropriate alarm sound to alert people in the vicinity of the fire.
- Control Panel: This serves as a central control unit that manages all alarm devices and displays information about the location and type of fire.
- Emergency Service Communication Device: In some systems, the system is connected to automatic communication devices with emergency services such as fire or ambulance when a fire is detected.
A fire alarm system is considered an essential part of safety equipment in buildings and facilities, playing a vital role in protecting lives and property from the dangers of fires.

11
Environmental Monitoring System
An environmental monitoring system is a specialized system designed to monitor and evaluate various environmental parameters in natural or industrial environments. This system utilizes a variety of devices and sensitive instruments to measure different environmental variables such as temperature, humidity, air pressure, air and water quality, soil, noise, radiation, and others.
Features of an Environmental Monitoring System include:
- Multiple Measurement Devices: These include devices for measuring various environmental variables such as temperature gauges, humidity meters, air quality monitors, and more.
- Recording and Documentation Systems: Data measured is regularly recorded and documented to provide an accurate record of environmental changes over time.
- Analysis and Reporting: It provides the capability to analyze measured data and generate detailed reports about the environmental condition, as well as offering necessary recommendations for improvement.
- Alerts and Alarms: It offers warning signals or alarms in case environmental parameters exceed specified limits, aiding in taking prompt actions to preserve the environment and human health.
Environmental monitoring systems are used in a wide range of applications including environmental monitoring for industries, factories, power plants, cities, rural areas, marine environments, and urban areas. This system contributes to understanding the environmental impacts of human activities and preserving the environment and natural resources.

12
Satellite Imaging Systems
Satellite imaging systems are used to capture images and spatial data of the Earth and outer space environments through satellites and spacecraft. These systems rely on high-resolution imaging equipment aboard satellites that capture detailed images of the Earth from orbits above.
Key features of satellite imaging systems include:
- Geographic Imaging: Satellite images enable the production of accurate geographic images of the Earth, used in aerial photography, location identification, and mapping.
- Environmental Monitoring: Satellite images are used to monitor environmental changes such as vegetation cover, water levels, land degradation, and climate change.
- Agricultural Use: Satellite images are utilized in agriculture to monitor farmland, identify suitable locations for farming, and estimate agricultural yields.
- Weather and Climate Observation: Satellite images help monitor weather conditions and forecast phenomena such as storms, hurricanes, and floods.
- Urban Planning and Infrastructure: Satellite images are used to identify urban growth areas and plan infrastructure for cities and urban regions.
By using satellite images, researchers and professionals in various fields can extract valuable data and information to analyze patterns and make informed decisions in areas such as environment, agriculture, weather, urban planning, and more.
